Blockchain Security: How Your Digital Data is Protected (A Beginner’s Guide)
In an increasingly digital world, the security of our data is paramount. From financial transactions to personal records, we rely on robust systems to keep our information safe from prying eyes and malicious attacks. Enter blockchain technology – a revolutionary innovation often praised for its inherent security features.
But what exactly makes blockchain so secure? Is it truly impenetrable? This long-form article will demystify blockchain security, breaking down the complex mechanisms that protect data on this groundbreaking distributed ledger. We’ll explore how cryptography, decentralization, and consensus work together to create a system that’s designed for trust and immutability, even for those new to the concept.
Understanding the Core: What is Blockchain?
Before diving into security, let’s quickly define blockchain in simple terms. Imagine a digital ledger, like a gigantic, shared spreadsheet, where every transaction or piece of data is recorded. Instead of being stored in one central location (like a bank’s server), this ledger is distributed across thousands of computers (called "nodes") worldwide.
Each "page" of this ledger is a "block" containing a list of transactions. Once a block is filled, it’s cryptographically linked to the previous block, forming a "chain" of blocks – hence, blockchain.
The Pillars of Blockchain Security: Why It’s So Robust
Blockchain’s strength doesn’t come from a single feature, but from a powerful combination of interdependent technologies. Let’s break down these fundamental pillars:
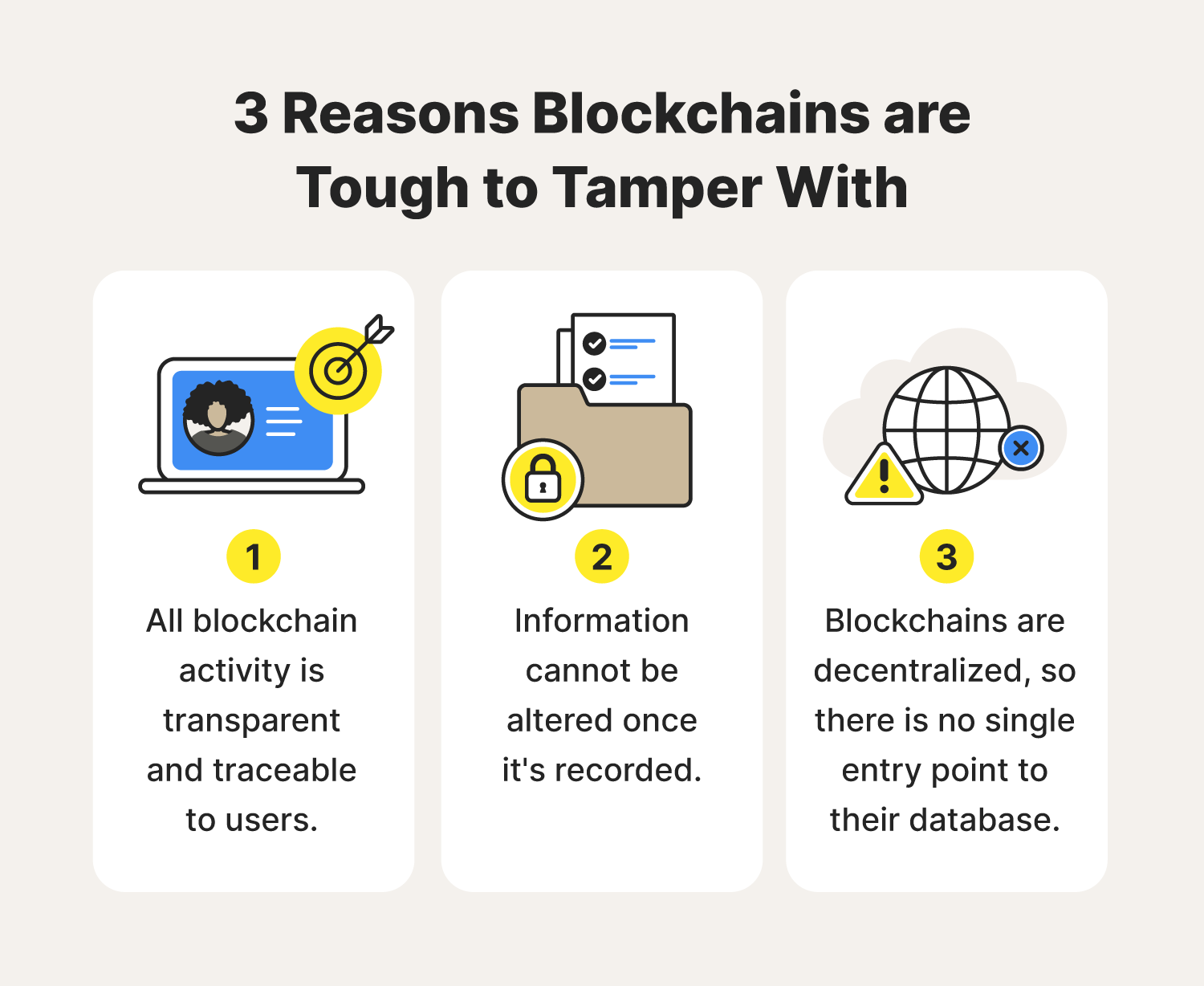
1. Decentralization: No Single Point of Failure
- The Concept: Unlike traditional systems where data is stored on a central server (a single target for hackers), blockchain distributes copies of the entire ledger across a vast network of computers (nodes).
- How it Protects Data:
- Redundancy: If one node goes offline or is compromised, thousands of other nodes still hold a complete and identical copy of the ledger. The system continues to function seamlessly.
- Attack Resistance: To alter data on a blockchain, a hacker would need to simultaneously attack and compromise a majority of the network’s nodes – a near-impossible feat on large, established blockchains like Bitcoin or Ethereum. This makes a "51% attack" (where one entity controls over half the network’s computing power) extremely difficult and costly.
- Trustless Environment: Because no single entity controls the network, users don’t have to trust a central authority. They can trust the network’s collective agreement and cryptographic proofs.
2. Cryptography: The Science of Secrecy
Cryptography is the backbone of blockchain security, using advanced mathematical techniques to secure communication and data. Two key cryptographic elements are crucial:
a) Hashing: The Digital Fingerprint
- The Concept: Hashing is a one-way mathematical function that takes any input (data, a document, a block of transactions) and turns it into a fixed-length string of characters – called a "hash" or "digital fingerprint."
- How it Protects Data:
- Uniqueness: Even a tiny change to the original data will result in a completely different hash. This makes it incredibly easy to detect if any data has been tampered with.
- Immutability Link: Each block in the blockchain contains not only its own hash but also the hash of the previous block. This creates a strong, unbroken chain. If someone tries to alter a transaction in an old block, its hash would change, breaking the link to the next block and immediately signaling tampering to the entire network.
- Efficiency: Hashes are much smaller than the original data, making them efficient to store and verify.
b) Public-Key Cryptography (Asymmetric Encryption): Digital Signatures
- The Concept: Every participant on a blockchain network has two mathematically linked keys:
- Public Key: Like your bank account number. You can share it with others; they can use it to send you data or verify your identity.
- Private Key: Like your bank account password. This must be kept absolutely secret. It’s used to "sign" your transactions, proving that you are the legitimate owner of the assets or data you’re trying to move.
- How it Protects Data:
- Authentication: When you initiate a transaction (e.g., sending cryptocurrency), you use your private key to create a digital signature. This signature proves that you authorized the transaction and that it hasn’t been altered since you signed it.
- Non-Repudiation: Once a transaction is signed with a private key and added to the blockchain, the sender cannot later deny having sent it.
- Confidentiality (Selective): While transactions are public, the identity of the sender and receiver is often pseudo-anonymous, represented only by their public key addresses.
3. Immutability: Once Written, Forever Set
- The Concept: "Immutable" means unchangeable. Once a block of transactions is added to the blockchain, it cannot be altered or deleted.
- How it Protects Data:
- Tamper-Proof Record: Due to hashing and the linked-chain structure, any attempt to change a past transaction would require re-calculating the hash of that block and every subsequent block in the chain. Given the massive computing power involved in securing large blockchains, this is practically impossible.
- Historical Accuracy: Blockchain provides a permanent, verifiable history of all transactions. This is crucial for auditing, transparency, and building trust in data records.
- Integrity: You can be confident that the data you see on the blockchain is the original, unaltered record.
4. Consensus Mechanisms: Agreement is Key
- The Concept: In a decentralized network, there’s no central authority to validate transactions. Instead, the network relies on "consensus mechanisms" – rules and processes that all participating nodes follow to agree on the true state of the ledger.
- How it Protects Data:
- Validation: When a new block of transactions is proposed, nodes verify its legitimacy (e.g., ensuring the sender has enough funds, the signature is valid).
- Agreement: Only after a majority (or a specific percentage, depending on the mechanism) of the network agrees that the block is valid is it added to the blockchain. This prevents a single malicious actor from adding fraudulent transactions.
- Common Mechanisms:
- Proof of Work (PoW): (Used by Bitcoin, older Ethereum) Nodes (miners) compete to solve a complex mathematical puzzle. The first one to solve it gets to add the next block and earns a reward. The "work" makes it costly to try and cheat the system.
- Proof of Stake (PoS): (Used by newer Ethereum, Cardano) Validators are chosen to create new blocks based on how much of the network’s cryptocurrency they "stake" (lock up as collateral). If they try to cheat, they lose their stake. This is generally more energy-efficient.
How Data is Protected: A Step-by-Step Scenario
Let’s illustrate how these elements work together when a piece of data (e.g., a transaction) is added to the blockchain:
- Initiation: A user creates a transaction (e.g., sending crypto, recording a document).
- Signing: The user’s private key digitally signs the transaction, proving their ownership and authorization.
- Broadcast: The signed transaction is broadcast to the entire blockchain network.
- Verification: Decentralized nodes across the network receive the transaction. They use the sender’s public key to verify the digital signature and check if the transaction is valid (e.g., sufficient funds).
- Block Creation: Validated transactions are gathered into a new "block." This block also includes a cryptographic hash of the previous block in the chain.
- Consensus: Nodes participate in the consensus mechanism (e.g., Proof of Work or Proof of Stake) to agree on the validity of the new block.
- Addition to Chain: Once consensus is reached, the new block is officially added to the blockchain. At this point, it receives its own unique hash.
- Distribution: The updated blockchain (with the new block) is then replicated and distributed to all nodes on the network, maintaining the decentralized and identical ledger across the globe.
From this point on, the data within that block is immutable – permanently recorded and resistant to tampering.
Beyond the Basics: Advanced Security Features
While the core pillars are fundamental, blockchain technology is constantly evolving with additional layers of security:
- Smart Contracts: Self-executing agreements written directly into code on the blockchain. While they introduce new security considerations (bugs in code can be exploited), they also enable automated, trustless interactions that enforce agreement without intermediaries.
- Multi-Signature (Multi-Sig) Wallets: Require multiple private keys to authorize a transaction. This adds an extra layer of security, making it harder for a single point of compromise to lead to asset loss.
- Zero-Knowledge Proofs (ZKPs): Allow one party to prove that they possess certain information (e.g., they are over 18) without revealing the actual information itself (their birthdate). This enhances privacy while maintaining verifiability.
Addressing Common Misconceptions & Vulnerabilities
While blockchain is incredibly secure by design, it’s not entirely invulnerable. It’s crucial to understand its limitations:
- Human Error: The biggest vulnerability in blockchain systems often lies with the users. Losing your private key means losing access to your funds/data forever. Falling for phishing scams or using weak passwords can compromise your accounts.
- Smart Contract Bugs: If the code of a smart contract contains errors or vulnerabilities, it can be exploited by hackers, leading to significant losses. Auditing smart contracts is critical.
- 51% Attacks (Theoretical): On smaller, less decentralized blockchains, a single entity could theoretically gain control of over 50% of the network’s computing power (PoW) or staked assets (PoS). This would allow them to manipulate transactions or prevent new ones, though this is economically infeasible for major blockchains.
- Front-End Attacks: While the blockchain itself might be secure, the applications or websites that interface with it can have vulnerabilities (e.g., insecure web servers, malicious browser extensions).
- Oracles: Blockchains often need external data (e.g., stock prices). "Oracles" provide this data, but if the oracle is compromised or provides incorrect information, it can affect smart contract execution.
It’s important to remember: the blockchain’s core security mechanisms are robust. Most security incidents in the crypto space occur due to vulnerabilities in applications built on top of the blockchain, human error, or centralized exchanges that act as intermediaries.
The Future of Blockchain Security
The field of blockchain security is continuously evolving. Researchers are working on:
- Quantum-Resistant Cryptography: Developing new cryptographic algorithms that can withstand the immense computational power of future quantum computers, which could potentially break current encryption methods.
- Improved Consensus Mechanisms: Exploring more efficient, scalable, and secure ways for networks to reach agreement.
- Formal Verification: Using mathematical proofs to ensure that smart contract code behaves exactly as intended, minimizing bugs.
Conclusion: Trust Through Technology
Blockchain technology offers a groundbreaking approach to data security. By combining the power of decentralization, sophisticated cryptography (hashing and public/private keys), immutability, and robust consensus mechanisms, it creates a system that is inherently resistant to tampering and censorship.
While no system is 100% foolproof, blockchain significantly raises the bar for data protection in the digital age. It shifts trust from central authorities to verifiable code and a distributed network, paving the way for a more transparent, secure, and resilient digital future. Understanding these fundamental security principles is key to appreciating the transformative potential of blockchain across industries.


Post Comment